UFC 4-021-02NF
27 September 2006
change 1, 23 October 2006
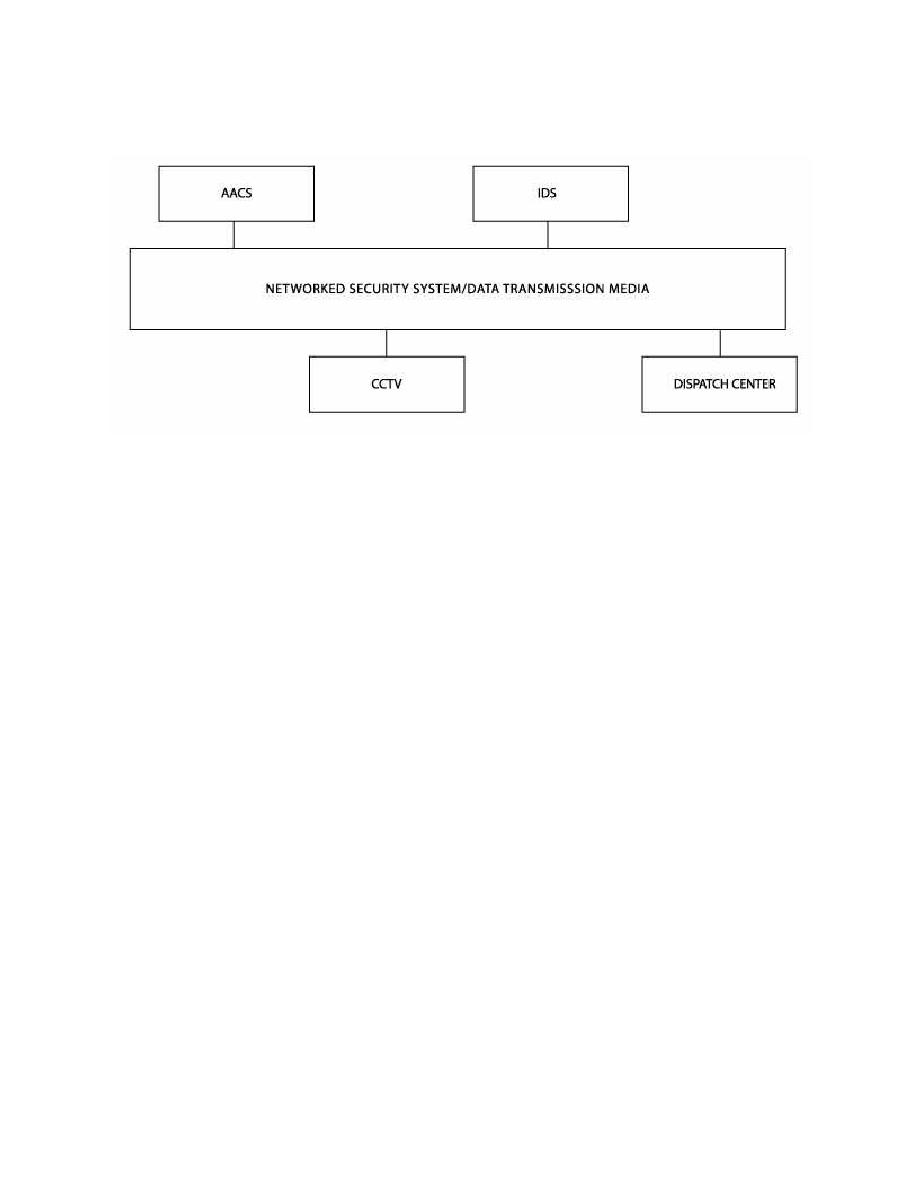
Figure 2-8. Networked System
The networked security system operates on a single network with drivers to the different
discrete components of the subsystems. While it is possible to procure networked
systems, security suppliers are at different stages of development of providing
networked systems for all ESS capabilities. At this writing, a lot of effort is being spent
by individual vendors of ACS, CCTV, IDS and DTM to partner with other subsystem
suppliers or write software drivers to achieve a networked ESS. Typically, networked
security systems are typically a Proprietary Security Network. Refer to Chapter 8, "ESS
Subsystem Integration" for more information.
2-5
MONITORING METHODS
2-5.1
General. Determine the alarm monitoring method early in the project
planning process. There are several different monitoring methods. Monitoring
configurations, as defined in DoD 0-2000.12-H, including local alarm, central station,
connection, and proprietary station. It is vital that the ESS designer understand the need
to identify the Dispatch Center and type of communications early in the project design.
2-5.2
Local Alarm. Local alarms actuate a visible and/or audible signal, usually
located on the exterior of the facility. Refer to Figure 2-9. Alarm transmission lines do
not leave the facility. Response is generated from security forces located in the
immediate area. Without security forces in the area, response may only be generated
upon report from a person(s) passing through the area or during security checks. Local
alarms may offer some deterrence value. Local alarm systems do not initiate the Detect,
Delay, Respond sequence.
20



 Previous Page
Previous Page
